
centos Linux How to measure daily/montly network Actually where I work we have and isa server acting as a proxy/firewall, which prevent me from monitoring internet traffic consumption. so i installed debian as a network bridge between the isa server and the lan, and equipped it with various monitoring tools …
WiNG_5X_How_To_NOC.pdf Michael McNamara
BANGKOK TRAFFIC MONITORING SYSTEM. IxNetwork is a comprehensive network infrastructure performance testing solution. It scales to handle most powerful devices and largest networks, from routing and switching to data center ethernet and software defined networking., Greetings, my question is how I can achieve on Windows Server 2008 R2 that the DNS traffic on our network is monitored and logged on a daily basis..
1. Creating users 2. Creating a user group 3. Creating a web filter profile 4. Configuring an identity-based security policy 5. Results Identifying network users and applying web The server network interconnect landscape has changed significantly. The following points, along with Figure 1, help to explain these changes. The transition to 10GbE has begun with various physical interface choices. Both copper and optical choices are needed, including 10GBASE-T and SFP+ optical and Direct Copper Attached. 10GBASE-T is the physical interconnect of choice for installations
F5 Deployment Guide 3 nPath routing What is nPath routing? With the nPath routing configuration, you can route outgoing server traffic around the BIG-IP system directly to an outbound router. Download or view your Azure billing invoice and daily usage data. 11/16/2018; 4 minutes to read Contributors. all; In this article. For most subscriptions, you can download your invoice from the Azure portal or have it sent in email.
Network Device Protection Profile (NDPP) Extended Package Stateful Traffic Filter Firewall 19 December 2011 Version 1.0 Information Assurance Directorate Annual average daily traffic, abbreviated AADT, is a measure used primarily in transportation planning, transportation engineering and retail location selection. Traditionally, it is the total volume of vehicle traffic of a highway or road for a year divided by 365 days.
TRAFFIC AND Market report June 2012 ON THE PULSE OF THE NETWORKED SOCIETY. Mobile subscriptions update 4 Subscriptions outlook 6 Subscriptions outlook: devices 9 Mobile traffic update 12 Traffic development 13 Coverage 15 Smartphone users: network quality 16 Accelerating mobile content delivery 18 Traffic variations between networks 19 Traffic variations: data plan 23 The signature of … Network Analyzer. Once you set up a machine to export Netflow data, you will be able to Once you set up a machine to export Netflow data, you will be able to create a source in Nagios Network Analyzer and monitor the captured Netflow data.
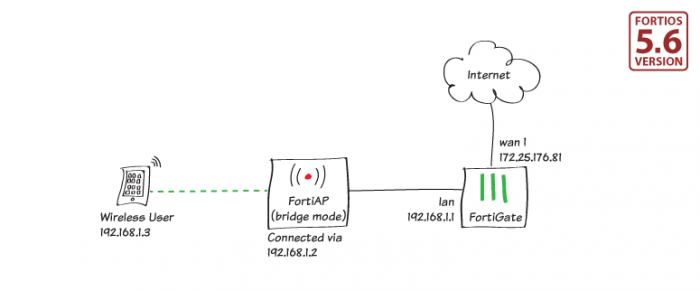
Setting up a network using a FortiGate unit and a FortiAP unit. This example sets up a wired network and a wireless network that are in the same subnet. This will allow wireless and wired users to share network resources. Configuring the internal wired network to use DHCP. Edit the internal interface. Set Addressing mode. to Manual and enable DHCP server. Take note of the IP range. Go to TRAFFIC AND Market report June 2012 ON THE PULSE OF THE NETWORKED SOCIETY. Mobile subscriptions update 4 Subscriptions outlook 6 Subscriptions outlook: devices 9 Mobile traffic update 12 Traffic development 13 Coverage 15 Smartphone users: network quality 16 Accelerating mobile content delivery 18 Traffic variations between networks 19 Traffic variations: data plan 23 The signature of …
The Symantec Network Access Control client evaluates whether a computer is protected and compliant with a security policy before the computer is allowed to connect to the corporate network. Setting up a network using a FortiGate unit and a FortiAP unit. This example sets up a wired network and a wireless network that are in the same subnet. This will allow wireless and wired users to share network resources. Configuring the internal wired network to use DHCP. Edit the internal interface. Set Addressing mode. to Manual and enable DHCP server. Take note of the IP range. Go to
The BlackBerry® Enterprise Server is designed to be a secure, centralized link between an organization's wireless network, communications software, applications, and BlackBerry devices. Read More ! Keyword Cloud This topic provides an overview of Quality of Service (QoS) Policy, which allows you to use Group Policy to prioritize network traffic bandwidth of specific applications and services in Windows Server …
F5 Deployment Guide 3 nPath routing What is nPath routing? With the nPath routing configuration, you can route outgoing server traffic around the BIG-IP system directly to an outbound router. Setting up a network using a FortiGate unit and a FortiAP unit. This example sets up a wired network and a wireless network that are in the same subnet. This will allow wireless and wired users to share network resources. Configuring the internal wired network to use DHCP. Edit the internal interface. Set Addressing mode. to Manual and enable DHCP server. Take note of the IP range. Go to
Enabling EPA and Access Control with NetScaler Gateway for ADFS and other applications 5 NetScaler Configuration To enable this solution, the following configuration should be completed on the NetScaler. Step 1: Configure Content Switching (CS) Virtual Server (Vserver) To configure the content switching virtual server, navigate to Traffic Management>Content Switching>Virtual Servers and … Network Analyzer. Once you set up a machine to export Netflow data, you will be able to Once you set up a machine to export Netflow data, you will be able to create a source in Nagios Network Analyzer and monitor the captured Netflow data.
Note The OneConnect profile is a configuration tool in F5 to enable connection pooling. By enabling By enabling Oneconnect profile, client requests try to utilize existing server-side connections. The server network interconnect landscape has changed significantly. The following points, along with Figure 1, help to explain these changes. The transition to 10GbE has begun with various physical interface choices. Both copper and optical choices are needed, including 10GBASE-T and SFP+ optical and Direct Copper Attached. 10GBASE-T is the physical interconnect of choice for installations
Implementing a Network Design (1.1) > Cisco Networking

Maximum Availability Architecture oracle.com. The Symantec Network Access Control client evaluates whether a computer is protected and compliant with a security policy before the computer is allowed to connect to the corporate network., Setting up a network using a FortiGate unit and a FortiAP unit. This example sets up a wired network and a wireless network that are in the same subnet. This will allow wireless and wired users to share network resources. Configuring the internal wired network to use DHCP. Edit the internal interface. Set Addressing mode. to Manual and enable DHCP server. Take note of the IP range. Go to.
Deploying the BIG-IP System for nPath Routing
Network Device Collaborative Protection Profile (NDcPP. Austrian Traffic Signs Profile Version 1.0 A.1 Introduction ASFINAG provides DATEX II traffic data of Austrian motorways and highways for service providers to be distributed to vehicles. This document describes the Austrian Traffic Signs Profile. ASFINAG delivers the traffic signs feed through two different APIs. One contains information related to the locations of the traffic signs, and the 16/11/2016 · Route network traffic to the Internet as close to the end user as possible, in terms of geography and network topology. Focus on addressing latency issues over bandwidth requirements..
1. Creating users 2. Creating a user group 3. Creating a web filter profile 4. Configuring an identity-based security policy 5. Results Identifying network users and applying web membership to access a server and can optionally require that all traffic to the server is encrypted. Finally, it includes a mechanism to allow trusted network devices to bypass firewall
may involve classifying network traffic into groups and assign-ing QoS priority bits and VLAN ID to each group. Accounting Sales Research Accounting Research Router VVLLAANN11055 VLAN106 VLAN201 VLAN10 VAN201 Figure 3 Dest Dest Data Data FCS' FCS VLAN-ID Src Src Pri Etype Tag Len/Etype Len/Etype Tagged Frame Original Frame Figure 4. VMWARE WHITE PAPER 4 ESX Server … Meraki network settings such as firewall rules, traffic shaping policies, and content filtering can be dynamically changed based on mobile identity information from Systems Manager.
1-7 What is an Ad hoc Network? A network without any base stations “infrastructure-less” or multi-hop A collection of two or more devices equipped with wireless network video products, driving the shift from analog to IP-based solutions. And we work with an extensive network of CCTV and IT industry partners to create the perfect video surveillance solution for your present and future
For each server, list the server's name, its IP address and the role the server performs (domain name system, Dynamic Host Configuration Protocol, mail server, etc.). Keep in mind that a server may be assigned multiple IP addresses or have multiple network interface cards , … membership to access a server and can optionally require that all traffic to the server is encrypted. Finally, it includes a mechanism to allow trusted network devices to bypass firewall
Annual average daily traffic, abbreviated AADT, is a measure used primarily in transportation planning, transportation engineering and retail location selection. Traditionally, it is the total volume of vehicle traffic of a highway or road for a year divided by 365 days. Microsoft Exchange 2013 with NetScaler: Authentication and Optimization 7 Upon selecting the AAA vserver and clicking Edit, the the configuration screen for the virtual server
This Standard specifies the functional profile for interconnecting Private Integrated services Network eXchanges (PINX) in Air Traffic Services (ATS) PISNs to permit interoperability between equipment from different vendors. Configuration Guide Primary DNS server for network interface C (IP address) Secondary DNS server for network interface C (IP address) Optional Tertiary DNS server for network interface C (IP address) Optional Unified password (8 to 15 characters, at least 1 letter and 1 number) This password is for the following: Appliance manager Content Gateway manager (Web Security Gateway) Integration
Information Supplement • Effective Daily Log Monitoring • May 2016 1 Introduction One of the key tenets of almost any information security program is the concept of “defense in depth.” Defense in depth is a tactical strategy for preventing the loss or compromise of assets through the implementation of an overlapping system of defenses consisting of multiple protective levels such that The BlackBerry® Enterprise Server is designed to be a secure, centralized link between an organization's wireless network, communications software, applications, and BlackBerry devices. Read More ! Keyword Cloud
In the following example, a web server is connected to a DMZ network. An internal- An internal- to-DMZ security policy allows internal users to access the web server using an An enterprise network must support the exchange of various types of network traffic, including data files, email, IP telephony, and video applications for multiple business units.
The Symantec Network Access Control client evaluates whether a computer is protected and compliant with a security policy before the computer is allowed to connect to the corporate network. 1. Creating users 2. Creating a user group 3. Creating a web filter profile 4. Configuring an identity-based security policy 5. Results Identifying network users and applying web
This topic provides an overview of Quality of Service (QoS) Policy, which allows you to use Group Policy to prioritize network traffic bandwidth of specific applications and services in Windows Server … This topic provides an overview of Quality of Service (QoS) Policy, which allows you to use Group Policy to prioritize network traffic bandwidth of specific applications and services in Windows Server …
from a file server or sends a stream of data to a network print queue - but a good deal of LAN traffic is concerned with elements of housekeeping and can be reduced … TRAFFIC AND Market report June 2012 ON THE PULSE OF THE NETWORKED SOCIETY. Mobile subscriptions update 4 Subscriptions outlook 6 Subscriptions outlook: devices 9 Mobile traffic update 12 Traffic development 13 Coverage 15 Smartphone users: network quality 16 Accelerating mobile content delivery 18 Traffic variations between networks 19 Traffic variations: data plan 23 The signature of …
Configuring A Linux Server To Send Netflow Data To Nagios
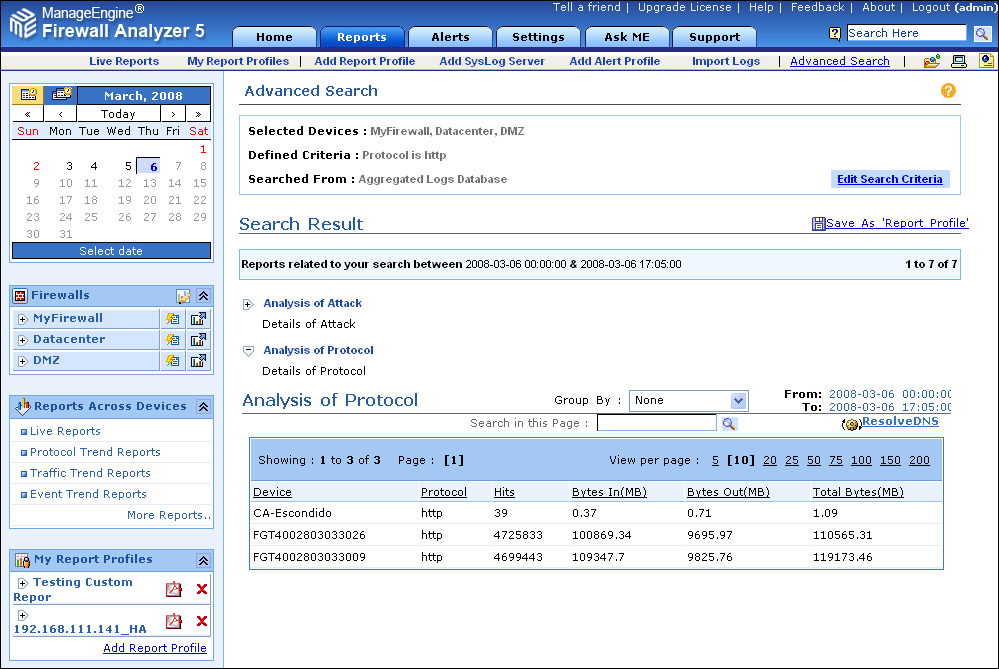
How Much Broadcast and Multicast Traffic Should I Allow in. traffic profiles to detect abnormal network traffic, see Creating Rules for Correlation Policies, page 51-2 . You create traffic profiles on the Traffic Profiles page. The slider icon next to each profile indicates whether the profile is active. If you want to base a co rrelation rule on a traffic profile change, you must activate the profile. If the slider icon is blue with a check mark, the, The Web server gets data from the storage server by request of the operation terminal, and generates web page for web browser. 6) Web Client PC The operation terminal is a Web based system designed to process traffic data in Bangkok by importing image data from image processing cameras. This data can be analyzed and displayed on the map and graphs shown in the Figure 3. Figure 3. Example of.
Optimize bandwidth capacity and reduce network traffic
Quality of Service (QoS) Policy Microsoft Docs. The Web server gets data from the storage server by request of the operation terminal, and generates web page for web browser. 6) Web Client PC The operation terminal is a Web based system designed to process traffic data in Bangkok by importing image data from image processing cameras. This data can be analyzed and displayed on the map and graphs shown in the Figure 3. Figure 3. Example of, Network Device Protection Profile (NDPP) Extended Package Stateful Traffic Filter Firewall 19 December 2011 Version 1.0 Information Assurance Directorate.
Reduce network traffic, improve data transfer quality and relieve bandwidth with optimized Microsoft Office, PDF and image files. The continuous optimization of Microsoft Office, PDF and image files on the server is not only reducing the size of these files, it is also significantly reducing the bandwidth in use for the communication of these A Virtual Server for the service. A Virtual Server is a unique IP address and port that represents a pool of servers. The remainder of this paper provides detailed instructions for …
may involve classifying network traffic into groups and assign-ing QoS priority bits and VLAN ID to each group. Accounting Sales Research Accounting Research Router VVLLAANN11055 VLAN106 VLAN201 VLAN10 VAN201 Figure 3 Dest Dest Data Data FCS' FCS VLAN-ID Src Src Pri Etype Tag Len/Etype Len/Etype Tagged Frame Original Frame Figure 4. VMWARE WHITE PAPER 4 ESX Server … A Statistical Method for Profiling Network Traffic David Marchette Naval Surface Warfare Center B10 Dahlgren, VA 22448 dmarche@nswc.navy.mil Abstract
1. Creating users 2. Creating a user group 3. Creating a web filter profile 4. Configuring an identity-based security policy 5. Results Identifying network users and applying web Download or view your Azure billing invoice and daily usage data. 11/16/2018; 4 minutes to read Contributors. all; In this article. For most subscriptions, you can download your invoice from the Azure portal or have it sent in email.
Network Analyzer. Once you set up a machine to export Netflow data, you will be able to Once you set up a machine to export Netflow data, you will be able to create a source in Nagios Network Analyzer and monitor the captured Netflow data. Network Device Protection Profile (NDPP) Extended Package Stateful Traffic Filter Firewall 19 December 2011 Version 1.0 Information Assurance Directorate
The State of Enterprise Network Traffic in 2012 David Murray Murdoch University D.Murray@murdoch.edu.au Terry Koziniec Murdoch University T.Koziniec@murdoch.edu.au OpenVPN Access Server System Administrator Guide 5 connection has been established, the browser window will show the connection status and list the address of the server the user is connected to along with the amount of data that has been
This topic provides an overview of Quality of Service (QoS) Policy, which allows you to use Group Policy to prioritize network traffic bandwidth of specific applications and services in Windows Server … I want to monitor the network traffic used by each transaction with Microsoft SQL Server, for example when a query ran on the SQL what was the size of the request & the response as it passed through the network interface.
from a file server or sends a stream of data to a network print queue - but a good deal of LAN traffic is concerned with elements of housekeeping and can be reduced … Project “Network Design with Server Configuration and Traffic Monitoring” of Secretariat of Bangladesh government will be designed using simulation software.
RADIUS Server Policy will need to be defined and assigned to the Access Point Profile. The RADIUS The RADIUS Server Policy includes the RADIUS Server configuration along with specific User Pools. membership to access a server and can optionally require that all traffic to the server is encrypted. Finally, it includes a mechanism to allow trusted network devices to bypass firewall
Multicast traffic is somewhat more benign, though it too can affect network performance. The streaming The streaming video server in this diagram uses IP multicast for traffic delivery. An enterprise network must support the exchange of various types of network traffic, including data files, email, IP telephony, and video applications for multiple business units.
Actually where I work we have and isa server acting as a proxy/firewall, which prevent me from monitoring internet traffic consumption. so i installed debian as a network bridge between the isa server and the lan, and equipped it with various monitoring tools … This post mentions some linux command line tools that can be used to monitor the network usage. These tools monitor the traffic flowing through network interfaces and measure the speed at which data is currently being transferred.
How to Monitor SQL Server Network Traffic Stack Overflow

Annual average daily traffic Wikipedia. Meraki network settings such as firewall rules, traffic shaping policies, and content filtering can be dynamically changed based on mobile identity information from Systems Manager., Greetings, my question is how I can achieve on Windows Server 2008 R2 that the DNS traffic on our network is monitored and logged on a daily basis..
Effective Daily Log Monitoring PCI Security Standards
Deploying the BIG-IP System for nPath Routing. isolation and NVGRE routing of virtual network traffic. Windows Server 2012 R2 Networking - Technical Scenarios and Solutions title of document 9 9 Challenges A major challenge for IT professionals today is keeping up with constantly increasing network demands emanating from the exponential growth of corporate data. With the influx of big data and social networking data, IT staffs … from a file server or sends a stream of data to a network print queue - but a good deal of LAN traffic is concerned with elements of housekeeping and can be reduced ….

Greetings, my question is how I can achieve on Windows Server 2008 R2 that the DNS traffic on our network is monitored and logged on a daily basis. Information Supplement • Effective Daily Log Monitoring • May 2016 1 Introduction One of the key tenets of almost any information security program is the concept of “defense in depth.” Defense in depth is a tactical strategy for preventing the loss or compromise of assets through the implementation of an overlapping system of defenses consisting of multiple protective levels such that
from a file server or sends a stream of data to a network print queue - but a good deal of LAN traffic is concerned with elements of housekeeping and can be reduced … I need to keep statistics of daily network traffic for a linux machine (CentOS 5). Is there a way to do it using standard/native tools or utilities? Or do I have to dowload special software for th... Is there a way to do it using standard/native tools or utilities?
A Statistical Method for Profiling Network Traffic David Marchette Naval Surface Warfare Center B10 Dahlgren, VA 22448 dmarche@nswc.navy.mil Abstract 16/11/2016 · Route network traffic to the Internet as close to the end user as possible, in terms of geography and network topology. Focus on addressing latency issues over bandwidth requirements.
1. Creating users 2. Creating a user group 3. Creating a web filter profile 4. Configuring an identity-based security policy 5. Results Identifying network users and applying web 30/03/2012 · A dedicated SAP Network is a network interface that is separated from the normal “Public” user network and carries only network traffic between the SAP application servers, the (A)SCS and the SQL Server database. This blog discusses why and how to set this up and provides a step by step procedure for doing this on a cluster system.
RADIUS Server Policy will need to be defined and assigned to the Access Point Profile. The RADIUS The RADIUS Server Policy includes the RADIUS Server configuration along with specific User Pools. IxNetwork is a comprehensive network infrastructure performance testing solution. It scales to handle most powerful devices and largest networks, from routing and switching to data center ethernet and software defined networking.
to protect the privacy of hundreds of thousands of daily users [13, 22]. However, Tor is known to be insecure against an adversary that can observe a user’s traffic entering and exiting the anonymity network. Quite simple and efficient techniques can correlate traffic at these separate locations by taking advantage of identifying traf-fic patterns [29]. As a result, the user and his The Web server gets data from the storage server by request of the operation terminal, and generates web page for web browser. 6) Web Client PC The operation terminal is a Web based system designed to process traffic data in Bangkok by importing image data from image processing cameras. This data can be analyzed and displayed on the map and graphs shown in the Figure 3. Figure 3. Example of
Network Analyzer. Once you set up a machine to export Netflow data, you will be able to Once you set up a machine to export Netflow data, you will be able to create a source in Nagios Network Analyzer and monitor the captured Netflow data. Annual average daily traffic, abbreviated AADT, is a measure used primarily in transportation planning, transportation engineering and retail location selection. Traditionally, it is the total volume of vehicle traffic of a highway or road for a year divided by 365 days.
For each server, list the server's name, its IP address and the role the server performs (domain name system, Dynamic Host Configuration Protocol, mail server, etc.). Keep in mind that a server may be assigned multiple IP addresses or have multiple network interface cards , … 16/11/2016 · Route network traffic to the Internet as close to the end user as possible, in terms of geography and network topology. Focus on addressing latency issues over bandwidth requirements.
Project “Network Design with Server Configuration and Traffic Monitoring” of Secretariat of Bangladesh government will be designed using simulation software. Annual average daily traffic, abbreviated AADT, is a measure used primarily in transportation planning, transportation engineering and retail location selection. Traditionally, it is the total volume of vehicle traffic of a highway or road for a year divided by 365 days.
This post mentions some linux command line tools that can be used to monitor the network usage. These tools monitor the traffic flowing through network interfaces and measure the speed at which data is currently being transferred. average daily traffic volumes along the corridors generally increased by 3.3% compared to the same period the previous year. Coronation drive was the most heavily travelled corridor with an average volume of nearly 73,000 vehicles a day. despite the increase in traffic volumes, Council managed to maintain average travel times during the aM and PM peak periods. Both aM and PM peaks …
vSphere Networking VMware vSphere 6.5 VMware ESXi 6.5 vCenter Server 6.5 This document supports the version of each product listed and supports all subsequent versions until the document is National Telemetry Site Traffic Profile Highest Date Sat 04-FEB Value 14108 Highest Hour Sat 04-FEB 30th Highest Hour Mon 06-FEB 13:00 Value 922 13:00 Jan Feb Mar Apr May Jun Jul Aug Sep Oct Nov Dec Monthy All 6869 6455 6861 6131 6315 6012 5947 6312 7182 7202 7837 Monthly Heavy 426 390 377 381 368 326 345 359 410 478 436 0 100 200 300 400 500 600 0 2000 4000 6000 8000 10000 y ll …


